
The proliferation of remote work and the increasing reliance on public Wi-Fi have created a significant security paradox, leaving professionals and their sensitive data exposed to threats that were once contained within the secure walls of a corporate office. As the boundaries of the workplace

Imagine a world where autonomous vehicles react to hazards in a split-second, where remote surgeries are performed with flawless precision across continents, and where smart cities manage traffic flow dynamically to eliminate gridlock. This isn't a distant dream but a reality being shaped by

The promise of augmented and virtual reality fundamentally reshaping the business world has echoed through corporate boardrooms for nearly a decade, yet its journey to mainstream adoption has been markedly slower than that of other disruptive technologies. While innovations like generative AI have

In an era where digital collaboration platforms have become the architectural foundation for modern business operations, understanding the nuances between service tiers is no longer a simple IT decision but a core strategic imperative. The Microsoft Teams platform represents a significant
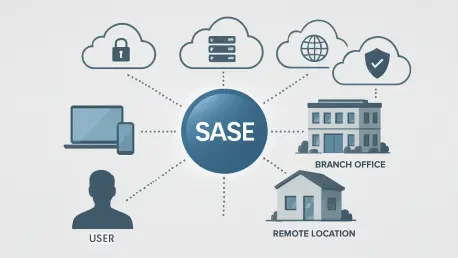
In an era where enterprise networks are increasingly distributed across multiple branches and remote endpoints, the challenge of maintaining consistent, high-level security has become more complex than ever before, prompting a significant shift toward Secure Access Service Edge (SASE) architecture.

For countless businesses, the prospect of modernizing an extensive and aging security infrastructure presents a significant financial and logistical challenge, often creating a barrier to adopting the advanced capabilities of today's technology. The conventional path involves a costly and