
Rethinking what 5G is really for If 5G is not a single fast lane but three distinct performance profiles, which one matched the needs of a streaming platform, a robotic arm, or a citywide sensor grid—and what happened when the wrong lane was chosen? That question shifted the conversation from

I’ve spent the last decade living at the seam where deterministic Ethernet meets modern wireless. Across brownfield plants and greenfield labs, my work has focused on turning TSN’s promises into practical reality over 5G. In this conversation, we dig into the craft behind microsecond-level

When breaches increasingly begin with valid credentials and trust shifts from networks to context-rich identity, the center of gravity in security moves from guarding walls to governing who and what crosses every digital doorway. That shift has turned identity and access management into the control
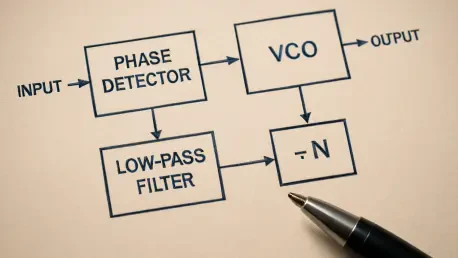
A fast way to know if your system is truly in sync Every tap that sends a message, every satellite fix that pins a location, and every clock edge that launches a CPU instruction rides on an invisible promise that two signals will agree not just roughly but precisely, in frequency and in timing, for

Imagine a fortress of data, meticulously guarded with the latest cybersecurity measures, only to be infiltrated not through the front gate but via a forgotten back door—a trusted vendor. In today’s interconnected business landscape, third-party breaches have surged, becoming a silent plague that

Cyber defenders feel the clock start the moment a hash dump surfaces, and in that race between exposure and remediation, Hashcat’s blend of speed, flexibility, and hard-earned pragmatism has become the tool that tips the balance for ethical password recovery and forensic analysis. In an era where